Hydra Host Launches the World's First Turnkey Intel TDX on Bare Metal Cloud
Run confidential AI workloads on bare metal, anywhere in the world—without having to trust your cloud provider. Perfect for regulated industries and sovereign data.
Beta Release: We're shipping early because we believe this capability matters more than waiting for polish. Expect some rough edges; we'll be iterating fast based on your feedback.
Hydra Host now offers one-click Intel TDX: we automatically provision a TEE-ready operating system and configure your server BIOS so you get a fully verified, confidential-computing-ready machine in less than 60 minutes on-demand.
No need for vendor docs. No BIOS spelunking. No "why isn't TDX initializing?" Slack threads.
Just:
- Select a server
- Select a TEE OS
Start your confidential workloads
What Hydra's Confidential AI Enables
With automated Intel TDX on Hydra, you can:
Launch confidential AI services globally Offer LLM APIs and ML inference where neither your models, data, context, nor prompts are visible to the underlying infrastructure.
Move regulated or high-sensitivity workloads to Hydra's cloud with cryptographic isolation Use hardware-backed confidentiality as part of your HIPAA / PCI-DSS / GDPR story.
Implement strong, hardware-rooted key management Release secrets only to attested TDX environments, effectively giving you HSM-like guarantees without separate hardware.
Build sovereign and regional offerings fast Stand up "trust-minimized" infrastructure in new regions without building local data centers or hiring local infra teams.
This is not just "more secure servers." It's an entirely new go-to-market capability: offer AI capabilities to customers who previously would only run on their own on-prem hardware.
Why Teams Choose Hydra for TDX
We believe we are the first bare metal provider in the world to offer turnkey Intel TDX—from BIOS to OS to attestation—fully automated for on-demand consumption.
The Old Model: "Just Trust Your Cloud"
For years, "moving to the cloud" has meant accepting an open secret the industry doesn't like to say out loud: your cloud provider can see everything you run.
Your data, your models, your prompts—all of it is technically accessible to their software stack and their employees. That's not a bug. That's the architecture.
When you spin up a VM, you're implicitly trusting that:
- The hypervisor won't inspect or tamper with your memory
- The host OS hasn't been compromised
- The cloud provider's admins won't peek at your data
- There's no successful hypervisor escape in the stack
That's not paranoia—that's the default trust model of virtualized infrastructure.
Intel TDX: A Secure Enclave for Your Workloads
Intel Trust Domain Extensions (TDX) changes this model completely.
TDX introduces Trust Domains (TDs)—hardware-isolated VMs where:
- The hypervisor and host OS cannot read your memory or CPU state
- Your VM memory is always encrypted in hardware
- You can remotely attest that your workload is running on genuine Intel hardware with the expected security configuration
Think of it as a secure enclave shaped like a full Linux VM.
You keep your existing tooling—SSH, containers, Kubernetes, GPUs—but now your workload is shielded, even from the cloud provider running the machines.
Why TDX Is a Big Deal for Real Workloads
1. The Hypervisor Is Out of the Trust Chain
Intel TDX on Hydra means no one has visibility into your workload except you.
That dramatically reduces risk from:
- Malicious or careless insiders
- Hypervisor escape vulnerabilities
- Compromised host OS
2. Confidential Computing Without Rewriting Your Stack
Early confidential computing (SGX) was powerful but painful:
❌ Special enclave SDKs
❌ Limited memory
❌ Awkward I/O
❌ Refactor your app or forget it
With TDX on Hydra, you get:
✅ Standard Ubuntu (24.04 LTS or 25.04)
✅ Unmodified applications—run your existing code as-is
✅ Hundreds of GBs of encrypted memory
✅ Normal VM workflows—SSH, systemd, containers, Kubernetes
✅ Full GPU passthrough
Confidential computing stops being a research project and becomes a checkbox on your deployment pipeline.
3. Zero-Trust Infrastructure, Actually Verified
TDX includes remote attestation: cryptographic proof of where and how your workload is running.
Your systems can verify that:
- They're running inside a genuine TDX environment on real Intel hardware
- Firmware and TDX module versions match your policy
- The measurement of the VM is exactly what you expect
- No tampering occurred before your secrets are released
This unlocks workflows like:
- "Only deliver TLS keys to an attested TDX host."
- "Only start this service if the hardware, BIOS, and OS match our golden profile."
- "Give auditors a cryptographically backed story of where sensitive data runs."
For regulated industries, this is the missing piece between "we think it's safe" and "we can prove it's safe."
4. The Killer App: Confidential AI
The most explosive use case we see is confidential AI.
With Hydra, you can:
- Run PyTorch, TensorFlow, vLLM, and other stacks inside a Trust Domain
- Attach NVIDIA GPUs for high-performance inference or training
- Keep both customer data and your models protected from the underlying infra
You can now sell high-trust AI services, globally, without owning your own data centers.
5. Sovereign, Regulated, and High-Sensitivity Cloud
Intel TDX on Hydra is built for teams who care deeply about jurisdiction and control:
- Governments and public sector
- Banks and fintech
- Healthcare and life sciences
- Enterprises dealing with cross-border data flows
TDX gives you:
- Hardware-enforced encryption of memory and CPU state
- Cryptographic attestation of your runtime environment
- Zero provider access by design
- A strong foundation for meeting HIPAA, PCI-DSS, GDPR, and similar obligations (with your own policies on top)
You get the elasticity of cloud with a trust model closer to owning the metal yourself.
The Catch: TDX Is a BIOS Puzzle From Hell
Here's the unglamorous part most marketing pages skip:
Getting TDX working on actual hardware is tricky and fragile.
On bare metal, manual TDX setup isn't just a matter of flipping a flag and going. It's more like a puzzle where every switch you toggle affects three others behind the scenes. You bounce between deep BIOS menus, turning features on, off, then on again—virtualization here, memory encryption there, some security feature that only works if another was disabled two reboots ago—until the platform finally decides it's TDX-capable.
Different server platforms:
- Call the same concept by different names
- Hide critical options in various submenus
- Require settings to be applied in a specific order, with a precise sequence of reboots
Miss one dependency, or get one toggle wrong, and TDX doesn't politely tell you what's broken. It just… never comes up. At lab scale, that's annoying; at rack-and-region scale, it turns into a real operational risk.
We've eaten this pain so you don't have to. Our team has wrestled TDX into production across multiple server platforms, documented every cursed BIOS quirk, and automated the entire sequence. That's the product.
With Hydra: It's a Single Button Click
Hydra takes the entire TDX BIOS + OS setup and automates it end-to-end.
When you select a TDX-capable machine on Hydra:
- Choose your OS (Ubuntu Plucky 25.04 TEE or Ubuntu Noble 24.04 LTS TEE)
- Click deploy
- Get back a verified, TDX-ready server in under an hour
Behind that button, Hydra:
- Detects the underlying hardware platform and its TDX capabilities
- Applies a validated BIOS profile that enables Intel TDX, TME, TME-MT, and SGX features recommended by Canonical's TDX reference stack
- Orchestrates the multi-stage reboot sequence automatically
- Deploys a pre-configured TDX host OS
- Verifies that the TDX module is initialized and healthy
- Marks the server ready only after it passes all checks
What used to take an expert 2–4 hours per server is now just minutes for anyone on your team.
Under the Hood: BIOS Settings We Enable For You
Instead of asking you to chase vendor documentation, Hydra applies a BIOS configuration that mirrors the Intel TDX host setup described in Canonical's tdx project.
At a high level, a typical configuration on a TDX-capable platform looks like this:
Under Socket Configuration → Processor Configuration → TME, TME-MT, TDX:
- Set Memory Encryption (TME) to Enable
- Set Total Memory Encryption Bypass to Enable (optional, for best host OS and regular VM performance)
- Set Total Memory Encryption Multi-Tenant (TME-MT) to Enable
- Set TME-MT memory integrity to Disable
- Set Trust Domain Extension (TDX) to Enable
- Set TDX Secure Arbitration Mode Loader (SEAM Loader) to Enable (allows loading Intel TDX Loader and Intel TDX Module from the ESP or BIOS)
- Set TME-MT/TDX key split to a non-zero value
Under Socket Configuration → Processor Configuration → Software Guard Extension (SGX):
- Set SW Guard Extensions (SGX) to Enable
Then save the BIOS settings and boot.
Hydra automates the equivalents of these steps across supported server platforms, using each vendor's out-of-band management interfaces under the hood. You never have to click through BIOS menus or remember which combination of flags has to be toggled for Intel TDX to come up cleanly.
Production-Ready TEE OS Images
Our TEE images are built on Canonical's official TDX release 3.3.
Each image ships with:
- TDX host stack pre-configured
- KVM with TDX support enabled
- Tooling for creating and managing Trust Domains
- Integration with Intel Tiber Trust Services for remote attestation
You don't need to assemble a custom OS image or chase a half-dozen kernel options; we've already done that work.
Verification: Prove Your Server Is TDX-Ready
On a Hydra TEE host, TDX isn't "probably enabled"—it's verified.
You can check it yourself:
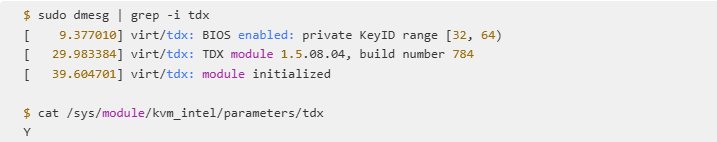
Hydra runs these checks automatically and will not mark a server ready until the TDX module is fully initialized and ready for you to use.
Get Started
We think confidential computing has been stuck in "interesting demo" territory for too long. This is our bet that it's ready for real workloads—and that bare metal is the right substrate to build it on.
Try it. Break it. Tell us what's missing.
Browse TDX-capable servers on Hydra →
Questions or custom needs? Visit hydrahost.com or reach out to our team.



